In an era where cyber threats are constantly evolving, organizations must be prepared for any potential breach. One of the most critical aspects of a robust security strategy is having a well-established incident response plan. This ensures that when security incidents occur, they are detected, contained, and resolved swiftly, minimizing the potential damage to the business. At Digi9, we employ industry-leading best practices in incident response to protect our clients’ digital assets, reduce downtime, and maintain business continuity.
Here’s a detailed look at how Digi9 ensures rapid and effective incident response for our clients:
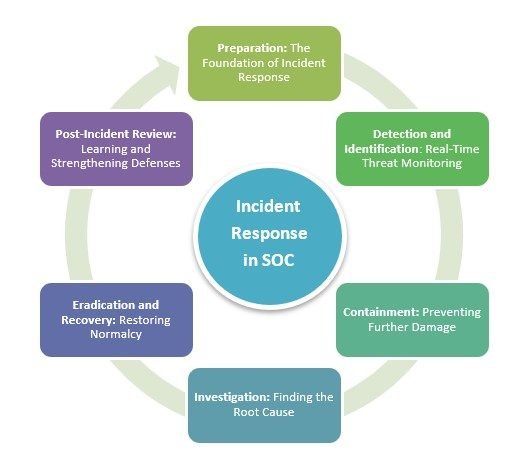
1. Preparation: The Foundation of Incident Response
Being prepared is essential for any successful incident response. At Digi9, we believe that proactive planning and preparation lay the groundwork for mitigating security risks. Our Security Operations Center (SOC) teams work with clients to build and maintain a customized incident response plan based on the organization’s unique needs, industry regulations, and threat landscape.
How Digi9 Prepares for Incidents:
- Risk Assessments: We regularly conduct vulnerability assessments and penetration testing to identify potential weaknesses in your infrastructure. This helps us understand where your systems may be most vulnerable to attack.
- Incident Response Plan (IRP): Digi9 collaborates with your team to develop a comprehensive IRP that includes detailed roles, responsibilities, communication strategies, and escalation paths.
- Training and Awareness: We believe that employee awareness is critical to security. Our team provides cybersecurity training to ensure that staff are aware of common threats like phishing and malware, and know how to respond in the event of an incident.
2. Detection and Identification: Real-Time Threat Monitoring
The faster a security incident is detected, the sooner the response can begin, reducing the potential impact. At Digi9, we employ real-time threat detection using state-of-the-art tools and advanced monitoring systems, such as SIEM (Security Information and Event Management) and EDR (Endpoint Detection and Response).
How Digi9 Detects and Identifies Threats:
- Continuous Monitoring: We constantly monitor network traffic and systems across your environment to detect any unusual activity or behavior that could indicate a potential threat.
- Anomaly Detection: Our SOC analysts use advanced algorithms and machine learning to identify anomalies that may suggest a security event, such as unusual login attempts, abnormal data transfers, or unauthorized system access.
- Alert Systems: Digi9’s systems are designed to trigger alerts in real-time, ensuring that SOC teams are immediately notified of any suspicious activity, enabling rapid response.
Example: One of our clients noticed a spike in network traffic late at night, which was unusual for their business. Using our SIEM tools, we identified a potential data exfiltration attempt and immediately flagged it as a threat. This real-time detection enabled us to act quickly, preventing sensitive data from being stolen.
3. Containment: Preventing Further Damage
Once a security incident is detected, the next step is containment isolating the threat to prevent it from spreading throughout the network. This is where Digi9’s SOC team excels, leveraging automation and manual responses to ensure swift containment.
Digi9’s Approach to Containment:
- Isolating Affected Systems: When an incident is detected, our team immediately isolates compromised devices to prevent the threat from spreading to other systems within the network.
- Blocking Malicious Traffic: We block any malicious IP addresses or unauthorized traffic to stop further infiltration or exploitation of vulnerabilities.
- Using SOAR for Automation: At Digi9, we employ SOAR (Security Orchestration, Automation, and Response) tools to automate routine containment processes, such as quarantining infected devices or blocking certain protocols, speeding up the response time.
Example: During a ransomware attack at one of our client’s facilities, Digi9’s SOC team quickly isolated the infected systems and blocked the ransomware from spreading to critical infrastructure. This containment allowed the client to avoid extensive downtime and prevented further data loss.
4. Investigation: Finding the Root Cause
After the threat is contained, the next critical step is to investigate how the attack occurred, what data or systems were affected, and who may be responsible. Digi9’s SOC team conducts a thorough forensic analysis to uncover the root cause of the incident and gather evidence.
How Digi9 Investigates Security Incidents:
- Forensic Analysis: We analyze logs, network traffic, and endpoint activity to trace the origin of the attack and understand its scope. This helps us determine how the threat actor gained access and what vulnerabilities were exploited.
- Malware Analysis: If malware was used, Digi9’s experts dissect the malicious code to understand its functionality, how it spread, and its intended impact.
- Collaborating with Law Enforcement: In cases of severe breaches, Digi9 works with law enforcement agencies to report the incident and share findings, ensuring proper legal procedures are followed.
Example: After containing a sophisticated phishing attack, Digi9’s forensic investigation revealed that the attacker had compromised an employee’s email account. Through detailed log analysis, we traced the attacker’s actions and provided the client with steps to further tighten their security measures.
5. Eradication and Recovery: Restoring Normalcy
Once the investigation is complete, the focus shifts to removing the threat from the environment and restoring affected systems to normal operations. Digi9 ensures this process is thorough and secure, minimizing any risk of re-infection.
Digi9’s Recovery Process:
- Removing Malware or Vulnerabilities: Our team ensures that all malicious software is completely removed from your systems and that any exploited vulnerabilities are patched to prevent future attacks.
- Restoring Systems: We restore compromised systems from clean backups, verifying that they are fully operational before reintroducing them into the network.
- Post-Recovery Validation: Before bringing systems back online, Digi9 performs rigorous validation checks to ensure the integrity and security of the recovered systems.
Example: After eradicating a trojan from a client’s network, Digi9 helped the client restore their systems from secure backups and implemented additional security measures to prevent future infections.
6. Post-Incident Review: Learning and Strengthening Defenses
Every incident is a learning opportunity. At Digi9, we conduct post-incident reviews to identify lessons learned, improve our incident response strategies, and enhance our clients’ overall security posture.
Digi9’s Continuous Improvement Process:
- Post-Incident Audits: We review how the incident occurred, how effectively it was handled, and identify any areas for improvement.
- Updating Incident Response Plans: Based on the findings from the review, we update the incident response plan to address new vulnerabilities or improve response protocols.
- Client Education: We share key insights with our clients, helping them understand the incident and what can be done to prevent future breaches.
Conclusion:
A robust incident response plan is essential for any business facing modern cyber threats. At Digi9, our commitment to best practices ensures that security incidents are swiftly detected, contained, and resolved by our expert SOC teams. By leveraging advanced technologies and proactive strategies, we help businesses minimize damage, reduce downtime, and maintain continuity in the face of evolving cyber risks. With Digi9’s incident response expertise, your business is always protected, allowing you to focus on growth while we handle your security.


