Incident response is a managed approach taken by organizations whenever there might be any detected breach or attack by cybersecurity, and it seeks to assess and reduce damage while their operations are restored in the shortest possible time.
With the progression of cybersecurity threats, companies must be better prepared to respond as a first reaction to incidents as they occur. An Incident Response Plan (IRP) is a guide for all stakeholders in proper handling and control of the consequences of cyberattacks, but an Incident Response Team (IRT) ensures that all the right people will be prepared to act when an incident occurs. Without such vital ingredients, a minor breach of security can immediately become a significant disaster.
Incident Response Plan (IRP)
Incident Response Plan is defined as an official document which describes a structured approach to the handling and management of incidents in systems or networks that have been hacked or infiltrated.
Key benefits of an IRP
- Fast detection of any incident and response that limit the damage
- Set rules and responsibilities help in smooth and efficient handling of any incident
- Most industries requires the organization to have an official incident response procedure, to meet their security standards
- Reducing the event disruption, an IRP can decrease breach-related cost; such costs include lawyers’ fees and fines and business loss.
Steps to Incorporate an Incident Response Plan
1.Risk Assessment:
Begin by conducting risk assessments that would outline the best threats your organization faces. It’s analyzing vulnerabilities that are derived from internal and external entities, such as ransomware or phishing attack or even supply chain attack. Your objective is to identify which are the most critical assets that need the highest level of protection.
2.Develop a Formal Incident Response Policy:
Develop a formal Incident Response Policy that outlines the approach that the organization uses to respond to security incidents. This policy shall define “what is an incident,” “who is responsible for managing the response,” and “what tools and resources will be needed.”
3.Develop an Incident Response Team (IRT):
An efficient Incident Response Team is the enabler to successful execution of the plan. The IRT should consist of representatives from various departments as IT, security, legal, human resource, and communications. Each team member should have well-defined responsibilities so that he or she knows what to do when an incident occurs.
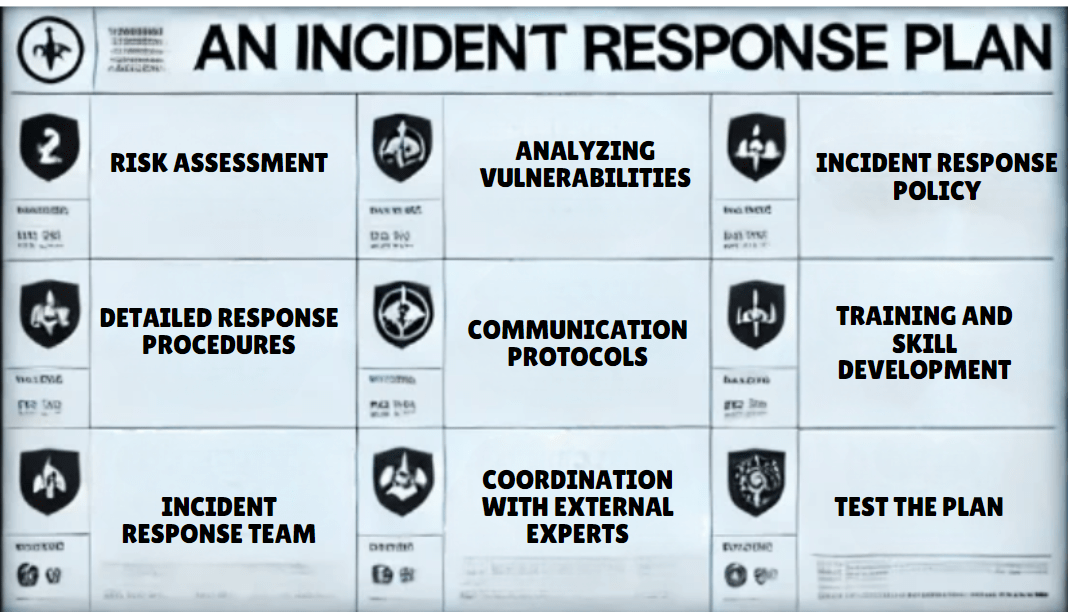
4.Develop Detailed Response Procedures:
The most essential part of the IRP is the sequence of detailed procedures to respond to various kinds of incidents. For example, you could have procedures dealing with malware infections, data breaches, and DDoS attacks. Each procedure must include steps of detection, containing, eradication, and recovery.
5.Establish Communication Protocols:
The response plan must contain well-established internal communication procedures between the IRT and senior management in addition to outward communication with stakeholders, customers, and regulators. For instance, when client information is incidented, the plan should elaborate on how to notify clients affected under breach notification legislations.
6.Test the Plan Periodically:
Once the IRP is developed, it undergoes constant testing by drills and simulations. Tabletop exercises and live incident simulations enable the IRT to train against a range of events, ascertain weaknesses in the plan, and effect appropriate improvements in the plan. Testing helps ensure that the team is prepared for actual events.
Formation of the Incident Response Team (IRT)
An efficient IRP demands competent and streamlined team building. The following should be considered while building IRT:
- Composition of Right Expertise: IRT will comprise technical and non-technical experts. Security analyst/forensic experts and IT professionals will handle most of the technical responses.
- Defining Responsibilities: Roles and responsibilities are clearly assigned among team members.
- Training and Skill Development and Replenishment: Includes staying abreast of current attack techniques and defense mechanisms in the constantly evolving threat landscape.
- Coordination with External Experts: Maintain contacts and contracts with trusted third-party responders before an incident occurs, like law enforcement or legal counsel
Roles in the IRT
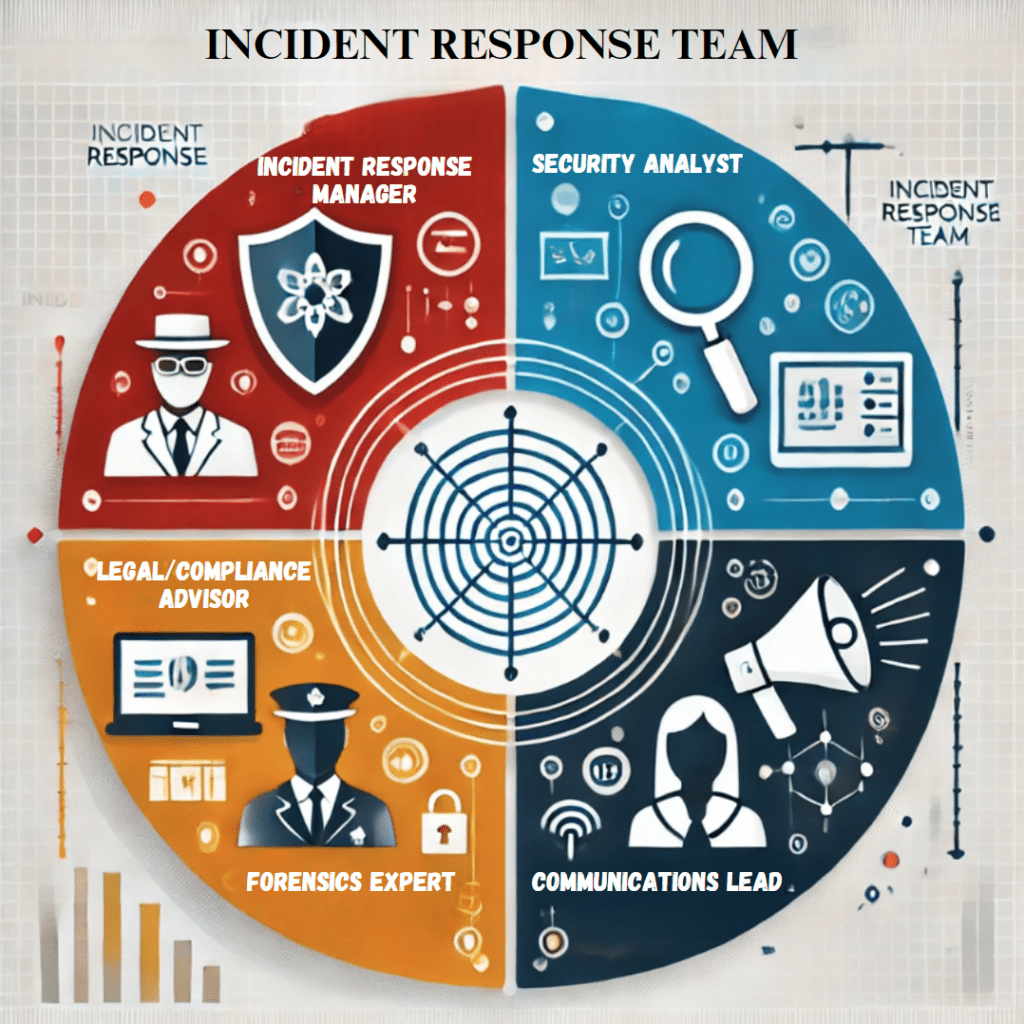
- Incident Response Manager: In charge of coordinating the overall responses in an effort made by him, which also includes strategic decisions and assures easy smooth communication.
- Security Analyst: Experts who specialize in detecting and analyzing incidents. It examines the alert messages, harbors the threat, and eliminates it.
- Legal/Compliance Advisor: It ensures that the response is in accordance with the legal and regulatory standards in place, especially where personal information is in question.
- Communications Lead: Oversees internal and external communication during an incident, including public relations and customer notification.
- Forensics Expert: An investigation to establish how such an incident happened and what damage ensued following an occurrence.
Incident Response Tools and Technologies
- Security Information and Event Management (SIEM): It aggregates security-related data from various sources and helps identify potential threats in real time.
- Endpoint Detection and Response (EDR): Informs organizations of suspicious activities taking place on its endpoint devices and automatically makes a response to threats.
- Digital Forensics tools: They are used for collection and analysis of evidence after an incident has taken place.
- Incident Response Platforms: These coordinate the response efforts so that teams can communicate and manage workflow during the event.
- Continuous Improvement: Review and update the plan periodically, to ensure the organization is up to date with all the threats and remediation.
Conclusion
According to The NIST Special Publication 800-61, Revision 2, Computer Security Incident Handling Guide it is best practice in today’s cybersecurity environment is the development of an Incident Response Plan as well as an able Incident Response Team. Those may invest in key tools and ensure they can respond quickly and effectively to incidents with a formal plan and the right team. Preparation not only limits the damage to be caused by cyberattacks but also maintains customer trust and compliance with regulatory requirements.


