In this digital age, network forensics is an activity that is critical in finding and analyzing network attacks. As cyber threats continue rising, organizations and security teams are focusing on the effective investigation of network activities to help detect, understand, and respond to intrusions. Below is a blog that delves into the basics of network forensics, importance in cybersecurity, and methods used to track down threats based on networks.
What is Network Forensics?
Network forensics is the capture, recording, and analysis of network traffic in search of patterns, suspicious activity, or network-based attacks. Part of a larger incident response and forensic investigation strategy, network forensics proves essential in tracking cybercriminals and understanding the events leading up to an attack.
Network forensics differs from other forms of forensics because it primarily involves dynamic data—information in transit across the network, not data stored on devices. This data is volatile and quickly disappears, and therefore, its real-time or near-real-time capture and analysis can be often necessary.
Why does Network Forensics Matter?
- Threat Detection: Network forensics helps in the detection of intrusions, unusual network traffic, and unauthorized access attempts.
- Incident Response: After an incident or in case of an incident, it helps analysts understand the scope and impact of an attack and guides effective containment and remediation, to know more about incident response, check this
- Compliance and Legal Proceedings: Network forensic data often plays a very important role in demonstrating compliance with cybersecurity regulations and can be used as evidence in legal actions.
- Improved Network Defense: Analysis of attacks shows weaknesses in defenses, thereby making future attempts less possible or easier to detect.
Key Elements of Network Forensics
Generally, the steps in the network forensic process include the following key steps:
- Traffic Capture: Traffic capture involves getting all traffic on the network, and this can involve packet data. This will be possible through the usage of taps on the network or port mirroring among others that may allow passive gathering of the traffic.
- Traffic Analysis: The traffic is then analyzed for any kind of unusual patterns, suspicious IP addresses, or anomalous behavior that may indicate an attack.
- Packet Inspection: DPI is the analysis of the contents of individual packets to detect malicious signatures or anomalous behavior.
- Log Correlation: Network logs are correlated with other data sources, such as firewall logs, application logs, and user activity, to create a complete picture of network activity.
- Data Reconstruction: Reconstructing data streams from fragmented packets to understand the actual data exchanged during the attack.
Network Forensic Tools
Several tools help in capturing and analyzing network traffic:
- Wireshark: A widely used open-source network protocol analyzer for capturing and inspecting packet data, u can download it here.
- tcpdump: command-line utility used to capture packets on the network. Packet analysis normally goes along with wireshark.
- NetFlow/SFlow: tools that collect and process net flow and s flow which can provide info about amount of data traveling through any given area, from whom, and to whom.
- Snort: open-source intrusion detection/prevention software that can run real time traffic analysis besides packet logging.
- Splunk: A log management and analysis tool, useful for correlating network activity logs and identifying attack patterns.
Common Network Attacks and Their Forensic Analysis
Network forensics is invaluable in detecting and analyzing various types of network attacks. Let’s look at some common attacks and how network forensics can help:
1. Distributed Denial of Service (DDoS) Attacks
- Explanation: DDoS attacks overload a network with traffic in an attempt to disrupt services.
- Forensic Analysis: Network forensics can trace back where the traffic flood originates from, which may include source IP addresses, botnet activity, time duration, and extent of the attack. The above can be discerned using NetFlow patterns from the traffic, thus giving a clue that this traffic is not normal user-generated traffic.
2. Man-in-the-Middle (MitM) Attacks
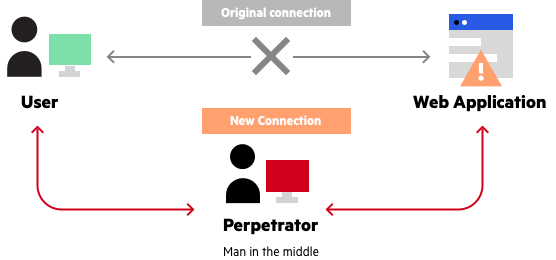
- Description: Malwares are computer programs. Through MitM attacks, attackers often intercept data between any communicating parties, and often will alter it in flight as well.
- Forensic Analysis: Identification of change in packets is done, as well as unordered routing of packets as evidence of the MitM. In forensic analysis tools can also provide decryption options with SSL/TLS tools to carry on with further analysis while taking care that the protocol to be checked is valid against a certificate.
3. Malware and Ransomware Infections
- Description: Malware or ransomware in the network can steal data, lock files, or even shut down systems.
- Forensic Analysis: Network forensics will help track malware spread throughout the network. This will help in tracing source IP and track strange outbound traffic toward external command-and-control servers. Deep packet inspection tools can easily catch signatures of malware present in packets.
4. Data Exfiltration
- Description: Hackers steal sensitive information from the network undetected for a long time.
- Forensic Analysis: Network forensics can detect exfiltration by tracing abnormal data transfer, large file uploads, or abnormal access patterns. Correlating network logs with user activity also helps to determine whether it is an insider attack or if a compromised account is being used.
5. Phishing and Spear Phishing Attacks
- Description: Phishing is spoofed emails or websites in stealing credentials or sending malware.
- Forensics Analysis: Forensics can trace the origin of malicious emails and follows the communication with a phishing website. Login attempts and access time may point to accounts being compromised by successful phishing.
Challenges in Network Forensics
In as much as network forensics is critical, network forensics comes along with challenges:
- Data Volume: The sheer volume of data produced by network traffic is too big to capture and analyze in real-time.
- Encryption: With the proliferation of encrypted traffic, most forensic tools cannot inspect data without decryption, and this raises privacy and legal issues.
- Evasion Techniques: Attackers use packet fragmentation, tunneling, and polymorphic malware to evade detection, thereby complicating forensic analysis.
Resource Requirement: Storage and processing resources are a significant requirement, especially for large organizations that handle a large volume of traffic.
Best Practices in Network Forensics for Optimal Effectiveness
Some of the best practices for optimizing network forensics are as follows:
- Continuous Monitoring: Continuously monitor network traffic for suspicious activity. Such an approach allows for incident response quickly.
- Network Segmentation: Network segmentation separates sensitive information while keeping out free movement for potential attackers, making forensic easier if that occurs.
- IDS Usage: Tools like Snort or Suricata alert the security teams on any threat; thus, real-time difference can be made, and malicious traffic differentiated.
- Forensic Readiness: Be prepared for forensic analysis with protocols for data capture, preservation, and analysis so that evidence is there and can stand up in court.
- Constant Threat Intelligence: The network forensics needs constant threat intelligence to identify the new attack vectors and tactics. This will give malicious patterns to the forensic team for faster identification.
Conclusion
Network forensics forms an integral part of an effective cybersecurity strategy. Capturing, analyzing, and correlating network data helps organizations identify intrusions and understand attack paths. Though problems still abound in this area, such as volume of data and encryption, adherence to best practices and the use of powerful tools can really revamp the forensic capabilities of organizations. Network forensics will always remain one essential defensive tool as cyber threats continuously change toward the prevention of sophisticated attacks within a digitized environment.