The digital landscape is changing at the speed of light with regard to connectivity in today’s world. This means more threats and even more complex threats are prompting organizations to act ahead of these threats. While prevention is always necessary, the capability to respond when breaches actually happen is just as important. It is here that digital forensics steps in as the cornerstone for more robust incident response strategies. Incident response is a managed approach taken by organizations whenever there might be any detected breach or attack by cybersecurity, and it seeks to assess and reduce damage while their operations are restored in the shortest possible time. Digital forensics reconstructs timelines of systems that have been breached, explains complex malware behavior, and provides critical evidence needed to understand, contain, and recover from security incidents. It is also instrumental in gathering intelligence that could help strengthen an overall security posture and, if required, aid in legal prosecution.
In this article, we’ll delve into the significance of digital forensics in incident response, how it integrates with the National Institute of Standards and Technology (NIST) Incident Response Framework, and why a proactive approach to forensics can drastically reduce the impact of cyberattacks.
The NIST Incident Response Lifecycle
The NIST Special Publication 800-61, Revision 2, Computer Security Incident Handling Guide, defines a four-phase incident response lifecycle to assist organizations in preparing for and responding to cybersecurity incidents. Digital forensics are important at most of these stages. In this section, we will discuss the incident response lifecycle and how digital forensics fit in at each stage:
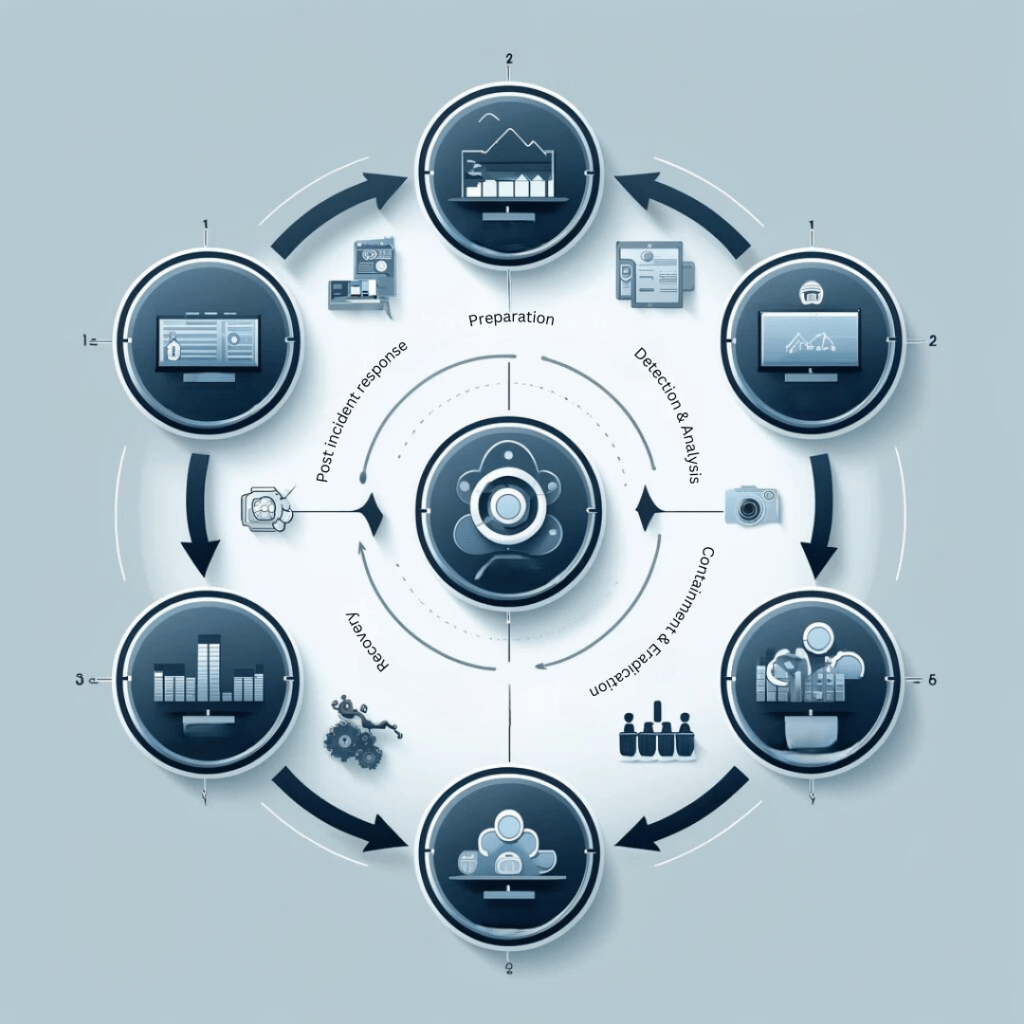
1. Preparation
Preparation is essentially the preventative phase where organizations initiate the tools, policies, and personnel with which to enact effective incident response. This can entail setting up incident response teams, definition of procedures, as well as getting ready with forensic tools that can be rapidly deployed at the occurrence of an incident.
Role of Digital Forensics in Preparation:
- Forensic Readiness: Organizations should be ready with forensic tools, like disk imaging software and log collectors that will help during the incident to gather evidence.
- Training and Awareness: The response teams should be trained in core concepts of forensic science: chain of custody, preservation of evidence, so that at least they do not contaminate the critical evidence.
Data Retention Policies: Implement relevant logs and data for a reasonable period. Such logs can be vital for forensic analysis after a breach.
2. Detection and Analysis
It is the recognition stage where the intrusion has been detected. Forensic teams then try to define and analyze the nature of the attack. Detection can be through IDS, firewalls, or endpoint protection tools that throw alarms whenever suspicious activity is noticed.
Role of Digital Forensics in Detection and Analysis:
- Evidence Collection: After detection forensic investigators collect the evidence from the affected systems, which includes log files, memory dumps, network traffic, and compromised files.
- Root Cause Analysis: The forensics indicate how the attack started and which method was used for it. Was there an exploitation of a vulnerability? Was there malware involved? Which mode did the attacker use to gain access?
- Evidence Triage: In an incident with big numbers, it is very important to triage some evidence earlier than others. For example, checking the attack vector first-that is, a phishing email-before delving deeper into other stages of the attack.
- Timeline Reconstruction: Digital forensics can reconstruct timelines of events that led to the incident-a clear timeline from the time of breach to discovery of malicious activity.
3.Containment, Eradication, and Recovery
After the incident has been identified and analyzed, one should step in to contain the threat, eradicate malicious activity from the system, and recover the organization to normal operation.
Digital Forensics in Containment, Eradication, and Recovery:
- Containment Strategy: Here, forensics determines which systems or data have been compromised. Such identification denotes which devices need to be isolated, which servers shut down, and which accounts disabled.
- Malware Eradication: Because forensics can identify all malicious files, registry changes or backdoors the attackers left behind, nothing is missed in cleanup efforts.
- System Recovery: In the recovery phase, forensic analysis ensures that the system is restored to a pre-attack state with no lingering threats. Forensic checks could also run on the backups before restoration to ensure that nothing has been altered.
4.Post-Incident Activity
Learning from the incident represents the final part of the NIST incident response process. This is the value of conducting investigations in digital forensics: findings from such investigations can be used to shape and improve security, effectively avoiding the occurrence of similar incidents in the future.
Role of Digital Forensics in Post-Incident Activity
- Incident Reports: The digital forensic teams document incidents, including whether it accessed through an attack vector, systems affected, methods used by the attacker, and evidence collected. This report will become important for legal use as well as enhancing security policies.
- Lessons Learned: Organizational Understanding of gaps in their security system which led to the incident is achieved through reviewing forensic evidence. This may evolve into better mechanisms of detection, patching vulnerabilities, or modifications in access control mechanisms.
- Legal and Regulatory Compliance: The forensic evidence is highly crucial for legal investigations as well as reporting to regulatory bodies in case of sensitive data and/or some violation of regulations.
Importance of Digital Forensics in Incident Response
Digital forensics can very well describe an incident vividly and therefore serves the following purposes:
- Correct Attribution: Forensics can identify the attacker or originator of the attack; if it is a disgruntled insider or an outside threat actor.
- Comprehensive Analysis: Detailed investigation by way of forensics will help understand the full impact of the attack, allowing the organization to respond accordingly.
- Forensic Evidence for Litigation Purposes: With theft of data or other forms of regulatory abuse, forensic evidence can be presented in court as evidence that such a breach indeed occurred and can serve as a tool in prosecutions.
- Future Defense Against Attacks: Forensics does not solve only the current problem but also provides insight that can be transformed into an enhancement in the security posture of the organization, thus lowering chances of future attacks on it.
Conclusion
Incorporating digital forensics into the incident response helps to understand, mitigate, and prevent a cyber attack. It will identify the threats, limit damage, and ensure legal compliance while providing insights that could strengthen defenses further in the future. Digi9 offers advanced digital forensic incident response services that assist organizations in bouncing back from incidents expeditiously and building a strong security posture overall.
References
- NIST Special Publication 800-61, Revision 2, Computer Security Incident Handling Guide.
- National Institute of Standards and Technology (NIST).


