Cyber Security

Introduction:
• Cyber security is the practice of protecting computer systems, networks, and data from unauthorized access, theft, or damage.
• What is Cyber Security: Cyber Security is consists of technologies process and controls designed to protect systems, networks, programs, devices and data from Cyber Security.
• Example: In an increasingly digital world, cybersecurity has become a fundamental concern for individuals and organizations alike. As we embrace technology in every aspect of our lives, from banking to healthcare, the risk of cyber attacks has grown exponentially.
Who Needs Cyber Security:
Cyber Security needs are Government, E-commerce, Legal requirements, Organizations, Healthcare etc…
1. Government:
Government sectors need cybersecurity to protect national security information.
2. E-Commerce:
A data breach or unauthorized access to customer information can significantly impact a company’s reputation and profitability.

3. Legal Requirements:
To protect personal data.
4. Organizations:
All organizations have sensitive data that cyber attackers want, and cybersecurity can help protect that data.
5. Healthcare:
Patient data is sensitive and valuable, so healthcare providers need to protect it.
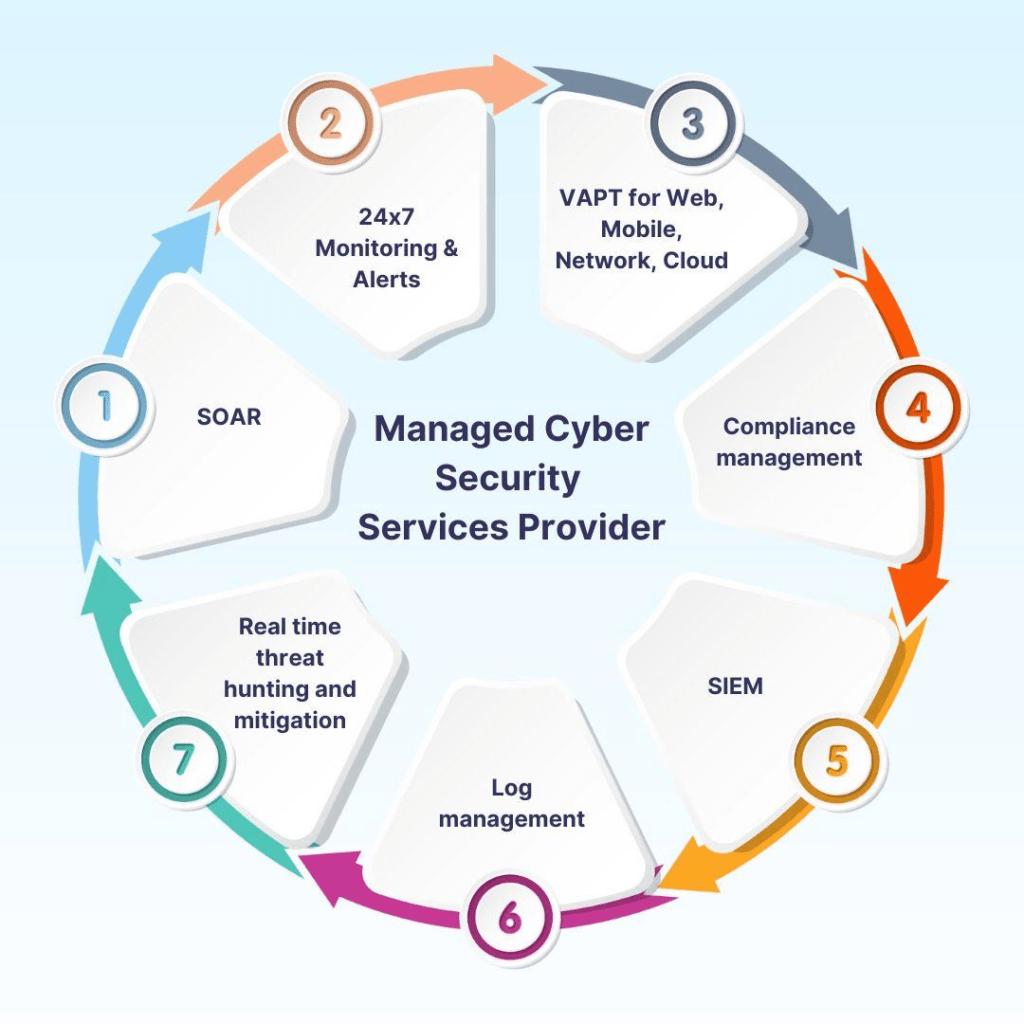
What Are Cyber Security Services:

1. SOAR (Security Orchestration, Automation, And Response):
It is the set of tools and technologies that help organizations manage and respond to security threats.
2. SIEM (Security Information And Event Management):
It is a solution that helps organizations detect and respond to security threats before they harm business operations.
3. Log Management:
The process of collecting, storing, and reporting system event logs to identify and respond to security threats.
Cyber Security Services Diagram
4. Compliance Management:
It is the set of policies and procedures that help an organization ensure it’s following all relevant regulations and industry standards for data protection and security.
5. Real Time Threat Hunting & Mitigation:
Real-Time threat detection and mitigation are critical components of cybersecurity strategies that help organizations stay ahead of cyber threats. Uses advanced technologies to monitor for threats in real time and provide automated responses.
6. VAPT for Web Mobile:
VAPT stands for Vulnerability Assessment and Penetration Testing, and is a security testing method that can be used to identify vulnerabilities in web applications, mobile apps, networks, and cloud environments. Assesses vulnerabilities in network infrastructure.
What are Cyber Security E (Subject Matter Expert):
Cyber security is important for SMEs because a cyber Attack can have a significant impact on their business, including: financial losses, reputational damage, business disruption, and customer distrust.
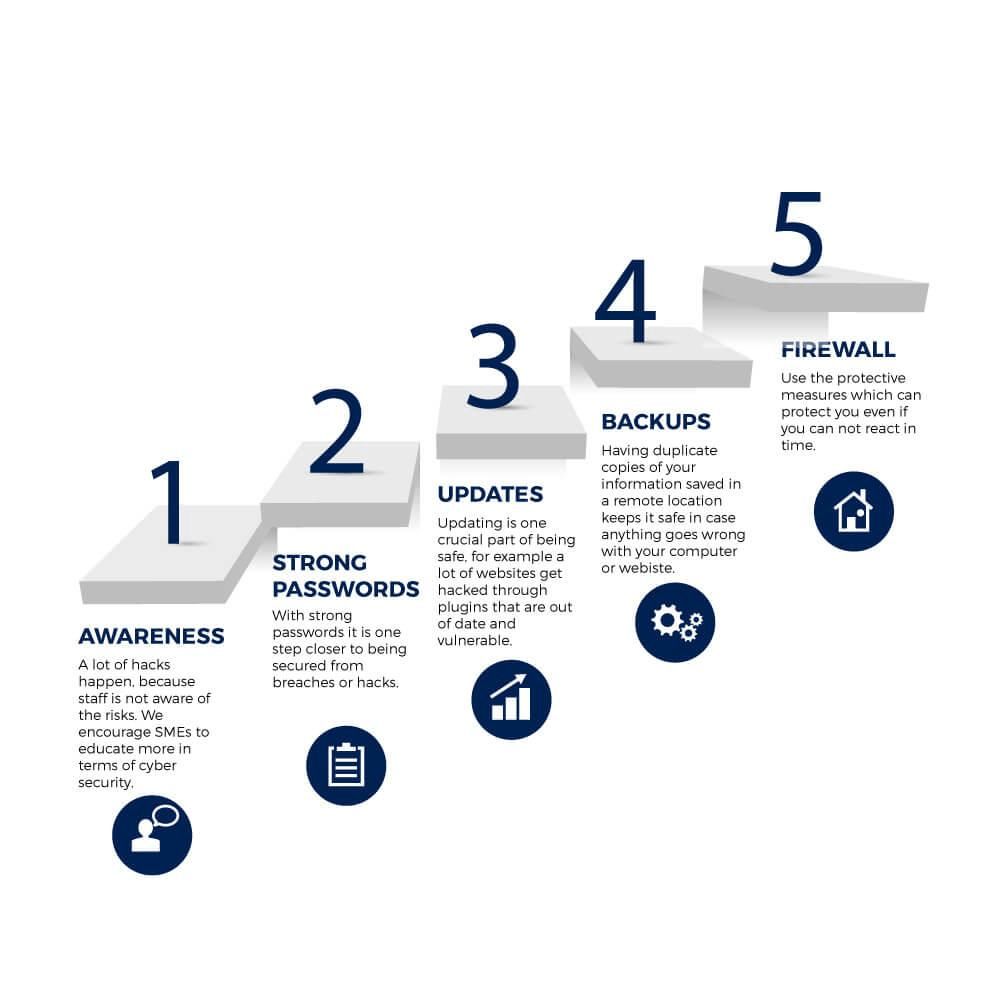
Diagram of Cyber Security SMS
1. Awareness:
Cybersecurity awareness is important for small and medium-sized enterprises (SMEs) because cybercriminals can exploit vulnerabilities to steal data, cause financial losses, and disrupt operations. Employees are often the entry point for cyberattacks, so it’s important to train them on cybersecurity awareness.
2. Strong Passwords:
Use a different password for each account. If one of your passwords is compromised, only that account will be affected. Use a combination of uppercase and lowercase letters, numbers, and symbols.
3. Updates:
Budget constraints: Budget constraints can make it difficult for SMEs to implement comprehensive cybersecurity policies. Low awareness of cybersecurity threats and measures can lead to weak protection strategies.
4. Backups:
Data Backup is a critical component of any cyber security plan for small and medium-sized enterprises (SMEs).Store backups offsite, such as in the cloud, to protect against physical disasters. Automate the backup process to reduce human error and ensure consistency.
5. Firewell:
It helps to protect a company’s network and data from unauthorized access. Firewall configurations should be regularly reviewed and updated to adapt to new threats. A cybersecurity solution that protects your computer or network from unwanted traffic coming in or going out.
4. What are Cyber Security Services:
1. Features:
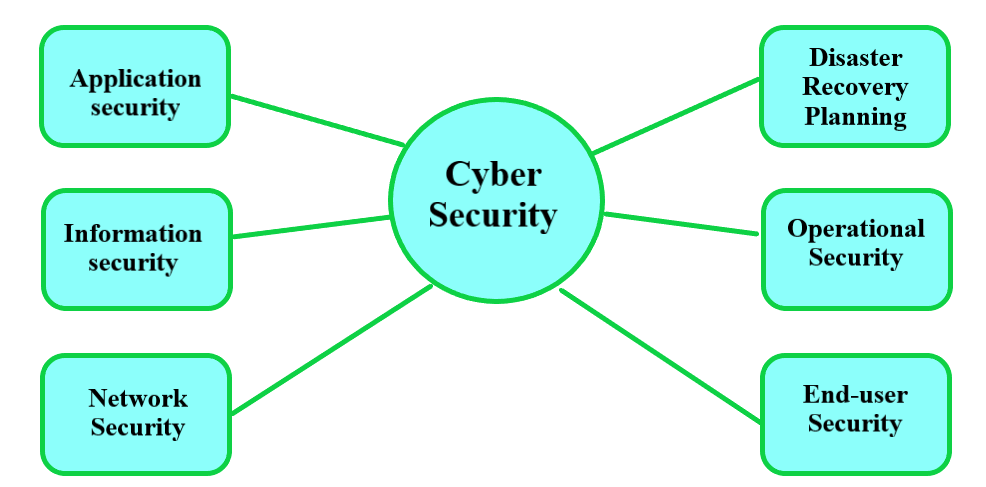
Cybersecurity platforms encompass features such as external threat protection, disaster recovery, identity access management, data encryption, cloud security, and comprehensive security analysis
2. Comprehensive Vulnerability Assessment:
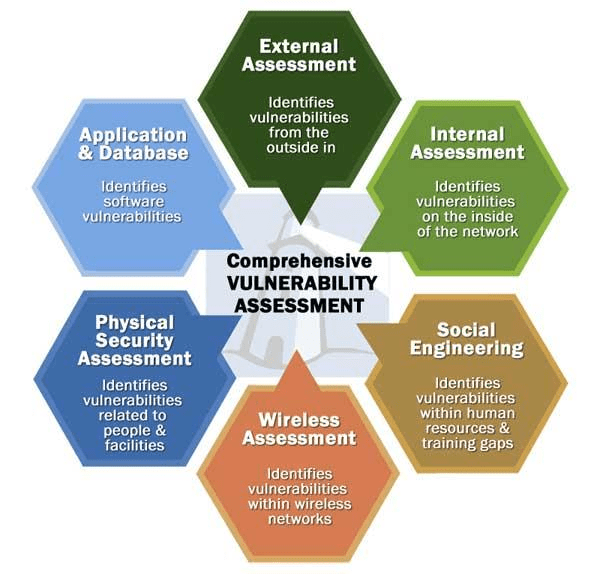
• A comprehensive cybersecurity vulnerability assessment is a systematic review of an organization’s IT systems, networks, and hardware to identify potential security weaknesses. It helps organizations protect their systems and data from unauthorized access and data breaches.
• A vulnerability assessment can help identify and prioritize risks, and recommend how to mitigate or remediate them. It can also help organizations verify the performance of third-party IT vendors.
3. Penetration Testing:
• Penetration Testing (or pen testing) is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system.
• In this blog we look at the five stages of penetration testing: Reconnaissance, Scanning, Vulnerability Assessment, Exploitation, and Reporting.

o Advanced penetration testing is a simulated cyber security testing to check for exploitable vulnerabilities present in the enterprise IT environment.
o Advanced Pen Testing involves attempted breaching of application systems or front-end/back-end servers to discover security vulnerabilities, such as unsanitized inputs that can be susceptible to code injection attacks.
4. Multi Platform Protection:
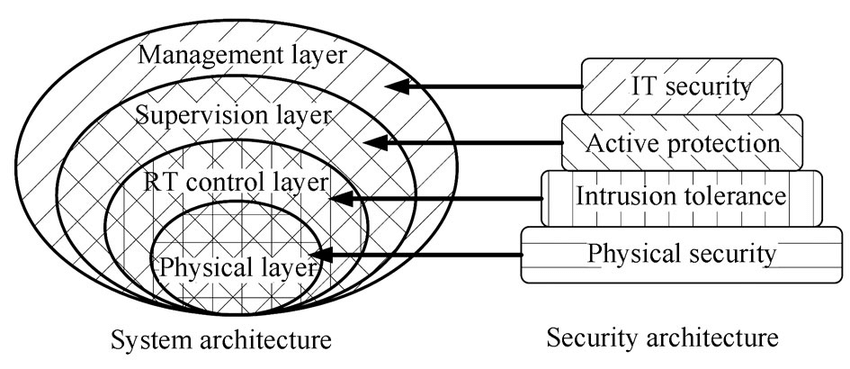
• Multi-layered security refers to securing your organization’s data using a variety of security measures.
• The idea is that if hackers want to access the data, they have to break through multiple layers of security.
• A multi-layer security architecture is sometimes referred to as defense-in-depth, helping to protect each touchpoint using tools purposefully built for that touchpoint.
• This element involves using physical devices or mechanisms to secure data access touchpoints.
5. Real Time Threat Monitoring:
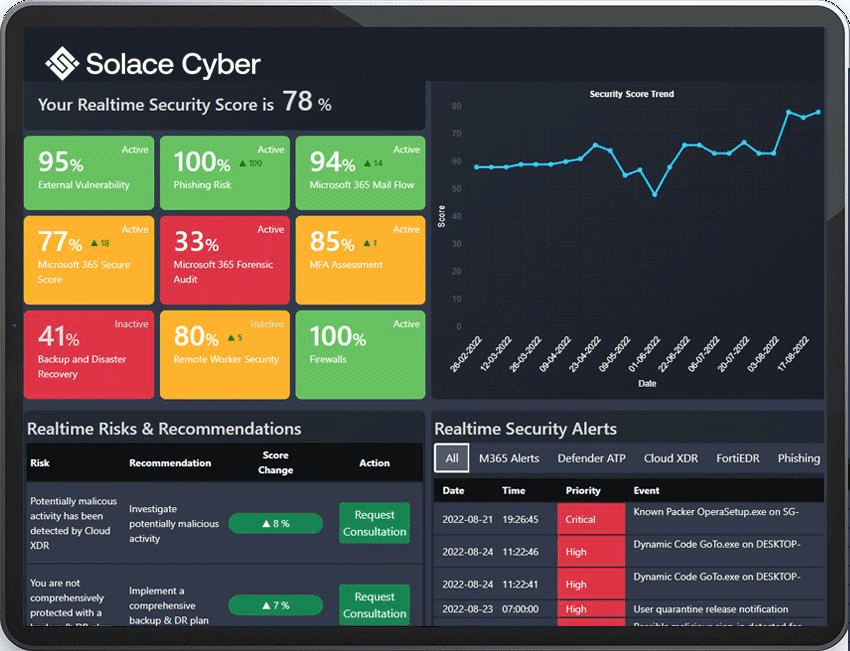
• Real-time cyber threat monitoring is a cybersecurity strategy that continuously scans an organization’s network for threats, vulnerabilities, and anomalies.
• It uses specialized tools and techniques to detect and respond to potential security breaches in real-time.
• Continuously monitoring diverse elements within an IT environment, including network traffic, system logs, endpoint devices, and applications.
• Real-time monitoring offers immediate insight into security events, allowing for a faster mitigation response.
• Organizations need to actively manage it to keep up with a fast-evolving cyber risk landscape.
6. Customized VAPT Services:
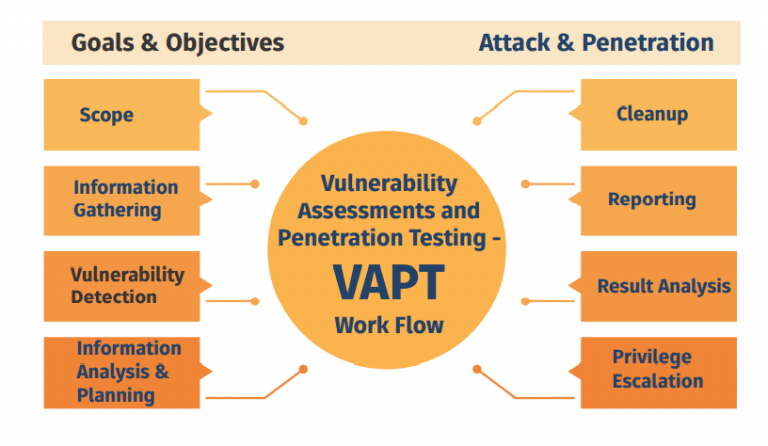
• VAPT stands for Vulnerability Assessment and Penetration Testing, and is a security testing method that can be used to identify vulnerabilities in web applications, mobile apps, networks, and cloud environments.
• Offers customized VAPT solutions for a variety of industries, including financial services, healthcare, technology, manufacturing, energy, government.
• Provides customized VAPT services that use advanced technologies to identify and mitigate risks.
5. Conclusion:
Cybersecurity is a collective responsibility: Cybersecurity is a dynamic field that requires the cooperation of individuals, developers, and organizations.
Cybersecurity threats are ever-present: Cybersecurity threats are a constant danger in the digital world, and the threat landscape is constantly evolving.
Cybersecurity requires a holistic strategy: A holistic cybersecurity strategy requires a combination of advanced security tools and human diligence.

