Introduction:
In the current digital landscape, cybersecurity has become a top priority for businesses in every sector. A crucial function of a Security Operations Center (SOC) is to keep an eye on security logs and scrutinize network traffic for any potential threats. At Digi9, we focus on assisting organizations in adopting advanced SOC practices to maintain the security of their networks. In this blog, we will explore the essential role that analyzing security logs and network traffic plays in protecting your business.
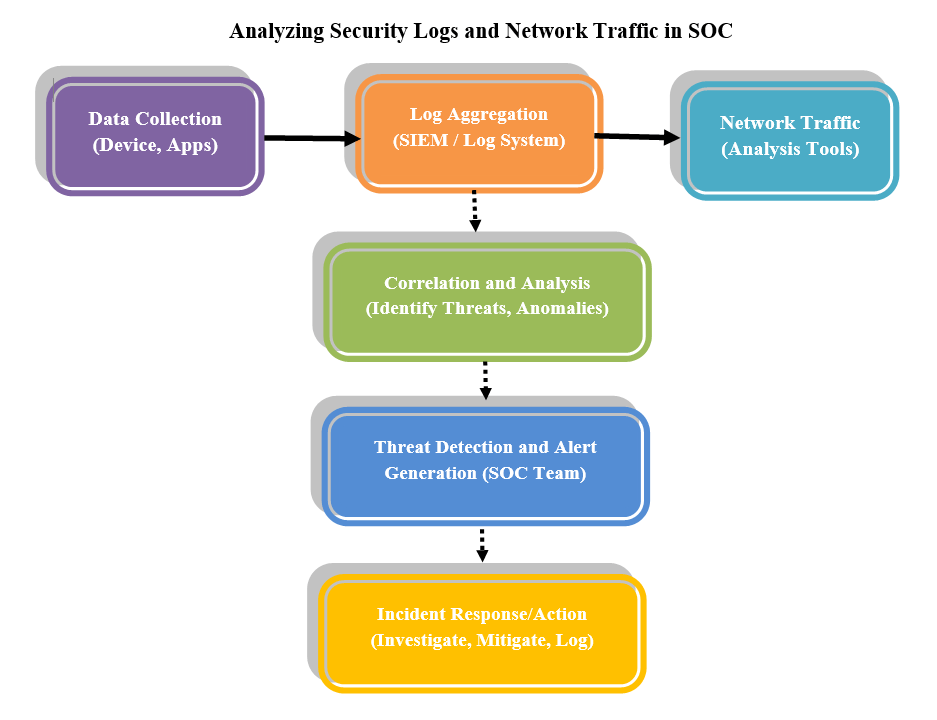
What are Security Logs and Why Are They Important?
Security logs capture events that take place within a system, network, or application. They provide essential insights into the interactions between users, applications, and devices on the network. By examining these logs, Digi9’s SOC team can:
- Detect unusual activities or anomalies: Security logs track actions such as logins, file access, and configuration changes. The Digi9 SOC team reviews these logs to identify unusual events, like multiple failed login attempts or unfamiliar access, which may signal potential threats.
- Identify and mitigate potential breaches before they escalate: By examining log data, the team can spot early indicators of breaches. They can swiftly address threats, such as malware or unauthorized access, to minimize any potential damage.
- Provide evidence for incident investigations: Logs offer a comprehensive record of events during security incidents. The Digi9 SOC team utilizes them to follow attack paths, identify affected systems, and determine compromised data, ensuring a complete investigation.
Example: For instance, if an unusual login attempt is detected from an unfamiliar location, Digi9 can analyze the logs to trace the login path, assess its legitimacy, and take appropriate action.
Network Traffic Analysis in SOC
Monitoring network traffic entails observing the flow of data across the network to spot any irregularities. This process enables Digi9 SOC analysts to:
- Identify malicious activities such as Distributed Denial of Service (DDoS) attacks or data exfiltration.
- Monitor bandwidth usage and recognize traffic spikes.
- Track the source and destination of data packets.
Example: In a real-time situation, Digi9 noticed a sudden increase in outbound traffic, which led to the detection of data exfiltration from a compromised system. Immediate measures were taken to isolate the system and avert further damage.
Tools Used for Log and Traffic Analysis
At Digi9, we employ top-tier tools to monitor security logs and analyze network traffic. Some of the tools we recommend include.
- SIEM (Security Information and Event Management): This system collects and analyzes logs fro6m a variety of sources.
- Network Traffic Analyzers: Tools such as Wireshark are essential for monitoring traffic in real-time.
- Intrusion Detection Systems (IDS): These systems identify unauthorized access or breaches by examining network traffic.
Challenges in Analyzing Security Logs and Network Traffic
While log and traffic analysis are vital, several challenges persist:
- Volume of Data: The massive number of logs generated can be daunting. Digi9’s SOC tackles this issue by employing automation and machine learning to highlight critical events.
- False Positives: Many harmless activities can trigger alerts. Digi9 aims to enhance detection algorithms to minimize false positives.
- Evolving Threats: Cyberattacks are continuously changing. Digi9 keeps pace by frequently updating threat intelligence and analysis techniques.
How Digi9 Can Help Your Organization
At Digi9, we possess the expertise and technology necessary to effectively monitor and analyze your security logs and network traffic. Our dedicated team of SOC professionals works diligently to identify threats, investigate incidents, and mitigate risks, ensuring your business remains protected around the clock.
Conclusion
Thorough log and network traffic analysis is essential for the security of any organization. At Digi9, we utilize cutting-edge tools and methods to provide ongoing monitoring and threat detection, assisting our clients in staying ahead of cyber threats. By partnering with us for your SOC needs, you gain a dedicated ally focused on safeguarding your systems.








