In today’s cybersecurity landscape, Security Operations Centers (SOCs) must remain proactive to detect and mitigate evolving threats. The MITRE ATT&CK Framework serves as a powerful tool for SOCs, offering a structured approach to analyze and respond to adversarial tactics and techniques. At Digi9, we empower organizations with advanced security solutions and help integrate frameworks like MITRE ATT&CK to strengthen their defenses. This blog explains the framework and its significance in SOC operations to give our clients a clear understanding of its value.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework (Adversarial Tactics, Techniques, and Common Knowledge) is an open-source knowledge base that categorizes the behavior of cyber adversaries. It provides insights into how attackers operate by breaking down the attack lifecycle into three critical components:
- Tactics: High-level objectives such as persistence, privilege escalation, or data exfiltration.
- Techniques: Methods attackers use to achieve these objectives, like phishing or command-line exploitation.
- Procedures: Real-world implementations of these techniques, showcasing variations used in attacks.
Digi9 integrates this framework into SOC operations to enhance threat detection, response capabilities, and overall security awareness.
Why is the MITRE ATT&CK Framework Crucial for SOC Operations?
- Enhanced Threat Understanding
By using the ATT&CK matrix, SOC teams can map attack behaviors to known techniques, enabling better visibility into potential threats. - Improved Incident Response
SOCs at Digi9 align incident response strategies with the ATT&CK framework, allowing for precise and efficient handling of cyber incidents. - Proactive Threat Hunting
Analysts can use the framework to proactively search for indicators of compromise (IOCs) and suspicious activity, stopping attacks before they escalate. - Optimized Tool Integration
We help clients align their existing security tools, such as SIEM and EDR, with the ATT&CK matrix to prioritize actionable alerts and reduce noise. - Continuous Improvement
Digi9 supports clients in using ATT&CK for gap analysis, ensuring their SOC capabilities evolve to counter emerging threats.
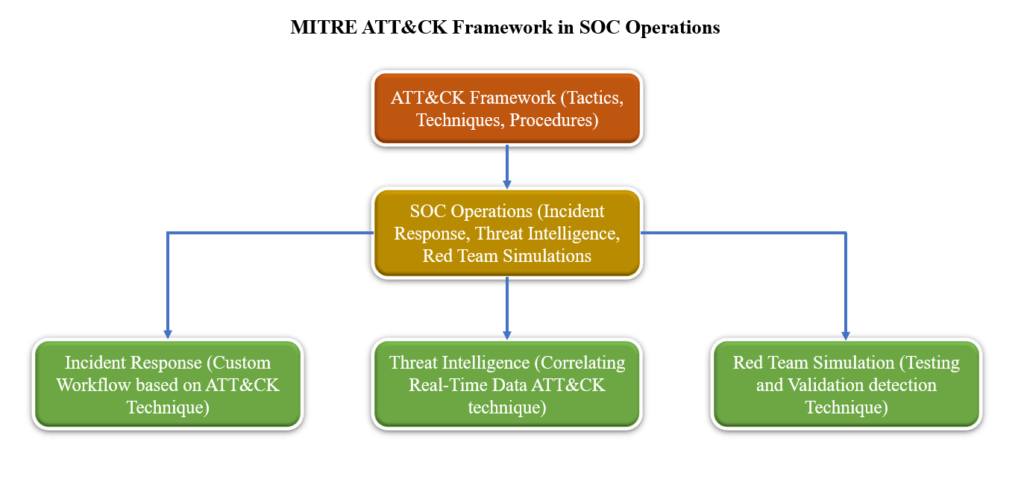
How Digi9 Uses MITRE ATT&CK to Strengthen SOC Operations
1. Incident Response Tailored to ATT&CK
At Digi9, we recognize that every cybersecurity incident is unique, so we tailor incident response workflows based on specific tactics and techniques identified in the MITRE ATT&CK framework. This allows us to address threats with precision and speed. For example, in a ransomware incident, our SOC quickly identified the tactic of “Credential Dumping” (T1003), which is commonly used to gain unauthorized access. By implementing the right mitigation strategies, such as isolating affected systems and blocking further credential exploitation, we reduced the impact within hours, demonstrating our rapid and effective incident response capabilities
Example: During a ransomware incident, our SOC identified tactics like “Credential Dumping” (T1003) and implemented mitigation steps within hours.
2. Threat Intelligence Integration
Integrating threat intelligence with the ATT&CK framework enables Digi9’s SOCs to rapidly correlate real-time data with known adversary tactics, techniques, and procedures (TTPs). This allows for faster and more accurate threat detection and response. For instance, when threat intelligence sources detect a technique like “Command-Line Interface Abuse” (T1059), we immediately configure our security tools to generate alerts and initiate monitoring rules that focus on this specific behavior. By aligning threat intelligence feeds with ATT&CK, we ensure that SOCs can quickly identify potential threats and respond effectively before damage is done
Example: If threat intelligence detects “Command-Line Interface Abuse” (T1059), our SOC immediately configures alerts and monitoring rules.
3. Red Team Simulations and Purple Teaming
Digi9 uses the ATT&CK framework to run realistic red team simulations and purple team exercises, which help test and improve clients’ detection and response capabilities. These simulations mimic actual adversarial techniques to identify gaps in defenses and strengthen incident response. For example, using techniques such as “Spear Phishing Attachments” (T1566.001), we test how well email security solutions perform against phishing attacks. The results not only highlight weaknesses but also provide actionable insights to enhance defenses, enabling our clients to be better prepared for real-world attacks
Example: Using “Spear Phishing Attachments” (T1566.001) during simulations to validate email defenses.
Steps to Leverage MITRE ATT&CK with Digi9
- Framework Familiarization
Digi9 provides training for SOC analysts to understand ATT&CK and how to apply it in daily operations. - Tool Integration
We help align your SIEM, EDR, and SOAR tools with the ATT&CK matrix to maximize detection accuracy. - Customized Threat Hunting Playbooks
Digi9 develops playbooks tailored to your organization, using the ATT&CK framework as a reference.- Regular Gap Assessments
Our team conducts assessments to ensure your SOC’s defenses align with the latest techniques in the ATT&CK matrix.
Conclusion
The MITRE ATT&CK Framework is a powerful tool that transforms SOC operations by providing actionable insights into cyber adversary behavior. It enables SOCs to detect, respond to, and mitigate threats with greater precision. At Digi9, we specialize in helping our clients integrate this framework into their operations to achieve stronger, more proactive security. Contact Digi9 today to learn how we can help safeguard your organization against evolving cyber threats







