As cyber threats grow more sophisticated, businesses need advanced strategies to protect sensitive data and systems. Network Access Control (NAC) has emerged as a critical technology to help organizations manage who and what can access their networks. At Digi9, we’re committed to helping clients secure their network environments, which is why we emphasize NAC as a foundational element in cyber defense. In this post, we’ll break down what NAC is, its significance in cybersecurity, and provide real-life examples to showcase its impact.
What is Network Access Control (NAC)?
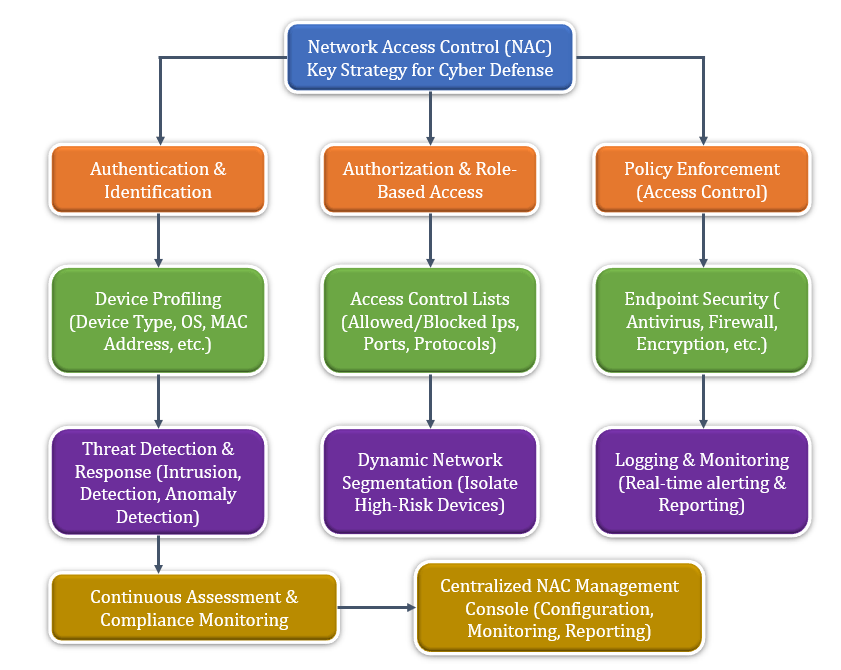
Network Access Control (NAC) is a security approach that regulates access to a network based on policies defined by an organization. Think of it as a digital gatekeeper that only allows authorized devices and users through. NAC solutions enforce policies that consider factors such as device type, compliance status, and user identity. This prevents unauthorized users and compromised devices from posing risks to critical systems.
NAC controls access by:
- Verifying Device Compliance: Ensures devices meet security requirements (e.g., updated antivirus, encryption).
- Identifying Users and Roles: Confirms user identities and grants access based on their roles or permissions.
- Segmenting Network Access: Restricts devices to specific areas of the network, reducing the spread of any potential threats.
Why NAC is Essential for Cyber Defense
Network Access Control offers a proactive defense against unauthorized access, reducing vulnerabilities within the network. Here’s why NAC is critical:
- Enhanced Security for Remote Work As remote work becomes the norm, employees often use personal devices or public Wi-Fi to access company networks, increasing exposure to risks. NAC can enforce compliance checks, verifying that devices meet the security requirements before connecting.
- Example: A financial firm implemented NAC to secure remote employee connections. Employees could only access sensitive resources if their devices had encryption enabled and the latest security patches. This reduced unauthorized access attempts by over 30%.
- Effective IoT and BYOD Management Many organizations now support IoT devices and Bring Your Own Device (BYOD) policies, increasing the variety of devices connected to the network. NAC helps manage this influx by monitoring and restricting device access based on compliance.
- Example: A healthcare provider implemented NAC to control access for IoT-enabled medical devices. By using NAC, they ensured that only approved devices could connect to their network, preventing data breaches and enhancing patient privacy.
- Immediate Threat Response NAC enables quick action if a device is compromised. For instance, if a malware-infected laptop attempts to connect, NAC can isolate the device, stopping the spread of the threat.
- Example: In a retail company, a compromised employee laptop was flagged by NAC for unusual activity. The system immediately restricted the device to a guest network with limited access, preventing sensitive customer data from exposure.
- Simplified Compliance with Security Standards NAC ensures that all connected devices follow company security policies, making regulatory compliance easier for organizations in industries such as finance, healthcare, and government.
- Example: A government agency used NAC to enforce compliance with stringent security standards. By checking device configurations, NAC helped them remain compliant with data protection regulations, avoiding potential fines and maintaining their clients’ trust.
Key Benefits of Implementing NAC
Here’s a closer look at the practical benefits of NAC for organizations:
- Reduced Attack Surface: By limiting access, NAC minimizes entry points for attackers, lowering the risk of breaches.
- Stronger Policy Enforcement: NAC enforces security policies consistently across devices and users, ensuring comprehensive protection.
- Network Visibility: NAC provides an overview of all devices and users, giving Digi9’s clients better insights into their network’s security status.
How Digi9 Can Help Implement NAC for Enhanced Security
Implementing NAC requires expertise to customize configurations and ensure ongoing compliance. Digi9’s team works closely with clients to design and implement an NAC strategy that aligns with their unique security goals. Our process includes:
- Assessing Security Needs: We evaluate the organization’s current setup to create NAC policies that match their requirements.
- Implementing Role-Based Access: We configure access based on roles, ensuring sensitive areas are restricted to authorized personnel.
- Continuous Monitoring and Support: We provide regular updates and monitoring to ensure the NAC solution adapts to emerging threats.
Real-World Success with NAC
Many businesses have already realized the benefits of NAC in preventing cyber threats and minimizing risk. Here are a few more real-world examples of NAC in action:
- University Network Security: A large university used NAC to manage access across multiple departments and student dorms. NAC restricted access based on user roles (staff, student, guest) and device type, ensuring that students couldn’t access sensitive administrative systems. This solution reduced incidents of unauthorized access by 40%.
- Manufacturing Plant Security: A manufacturing firm implemented NAC to secure IoT-connected machinery on its factory floor. By limiting network access to production control systems, NAC helped protect the organization from external cyber threats and minimized downtime by isolating any suspicious activity.
Future of NAC in Cybersecurity
As cyber threats evolve, NAC is set to remain a crucial element of cybersecurity. Emerging technologies like AI and machine learning are enhancing NAC capabilities, allowing faster and more accurate threat detection. AI-driven NAC solutions can learn from patterns, predicting and preventing unauthorized access before it occurs.
For businesses, NAC is not just about defense but about creating a resilient, adaptable network. At Digi9, we are committed to providing our clients with the tools and support they need to secure their network environments. We’re here to help organizations stay ahead of evolving threats while maximizing network visibility and control.
Conclusion
In a world where network security is essential, Network Access Control provides critical protection. By ensuring that only authorized devices and users access your network, NAC keeps sensitive data secure and safeguards your organization against a wide range of cyber risks.
If you’re interested in learning more about how Digi9 can help implement NAC for your organization, contact us today. Our team is here to help you take control of your network security and create a strong defense against cyber threats.


