Hashing is one of the best methods to provide data integrity and authenticate the digital evidence in the domain of digital forensics. Algorithms for hashing create digital “fingerprints” on files to detect even minimal changes made to data. This blog will explore the concept of digital hashing, its utilization in digital forensics, types of available hashing algorithms, and best practices for data integrity using hashing.
What is Digital Hashing?
Digital hashing is the process of taking a piece of data—such as a file, text, or an entire disk image—and changing it into a fixed-size string of characters, represented typically as a hexadecimal number. This unique “hash” is a digital fingerprint of the original data. The hashing process is deterministic, meaning that, given the same input data, the same hash will always be produced, while the smallest change in the data will produce a hash quite different from the original. Hashes in digital forensics ensure that evidence collected up to a point of presentation in a court of law has not been tampered with. Hash values can be recomputed through different stages to ensure nothing has been tampered with.
Why Digital Hashing Matters in Forensics?
Digital hashing, therefore, is important to digital forensics for some very important reasons:
- Data Integrity:
Hashes are a way to prove that evidence has not been tampered with. For example, in the collection of digital file, forensic experts generate its hash. During analysis or transmission of such evidence, the hash is generated again and compared to the hash during the time of collection. If it’s the same, then the data hasn’t been changed.
- Chain of Custody:
Hashing ensures that investigators show evidence to have been held securely from the time of reception into custody. In generating and recording hash values, each stage of the forensic process can be shown for which evidence has been kept under control, thus showing lower chances of a court case. To know more about chain of custody, check this
- Data comparison efficiency:
This allows for fast and effective comparison of large data sets. Rather than comparing every byte of two files, investigators can just check if their hash values match or if changes have been made.
- Verification of Digital Signatures as well as Malware Detection:
Another significant use of hashes is that of validating digital signatures, which verify the sources of data. Hash values are frequently used in malware analysis to identify known malicious files by comparing them with existing databases of malware hashes.
Types of Hashing Algorithms
Different hashing algorithms exist, with varying levels of security and uses. Some of the most common hashing algorithms used in digital forensics are listed below:
- MD5 (Message Digest Algorithm 5):
- MD5. 128-bit hashing algorithm for digital forensics use. It generates a hash of 32 hexadecimal characters. MD5 is one of the fastest and the lowest processing requirements hashing algorithms but unfortunately has collisions (a given two different files generating an identical hash). Hence not that secure. Though its popularity in digital forensics is high since it is fast and has very low processing requirements.
- SHA-1(Secure Hash Algorithm 1):
- SHA-1 generates a 160-bit hash. It was commonly used until vulnerabilities were found that allow collisions as well. Good security alternative but largely superseded by the stronger SHA-2 in most applications.
- SHA-2 Family (Secure Hash Algorithm 2):
- SHA-2 family consists of SHA-224, SHA-256, SHA-384, and SHA-512. It offers increasingly larger hash values as it grows from the name. In the forensics area, most uses are for SHA-256, a very strong cryptographic hash. The bigger one is much more time intensive than MD5 and SHA-1, yet this offers much better security.
- SHA-3(Secure Hash Algorithm 3):
- SHA-3 is the latest in the SHA family, which can provide more security without building on the same structure that SHA-2 does; therefore, it cannot fall victim to specific attacks. Though SHA-3 is not typically used much in digital forensics, its high security rate is increasingly bringing it to the mainstream.
How Hashing is Used in Digital Forensics
Hashing algorithms are mighty tools used in digital forensic investigations in many ways:
- Disk Imaging and Data Acquisition: While forensic investigators are creating an image of a hard drive or other storage media, they calculate a hash of the original data and the copy. Using the hash values, the investigators can confirm that the image is an exact duplicate and that no data was lost or altered during acquisition.
- File Integrity Verification: Forensic tools maintain and calculate hash values based on the files processed, where the integrity of the file can be verified with hash value recalculation any time during the case
- Evidence Validation at Court: Any digital evidence presented in court should demonstrate that it has not been altered since it is gathered. Hashing helps investigators to prove in the court that the integrity of the evidence has not been modified and thus enhances its acceptability and credibility.
- Malware Detection and Analysis: Hash values can be used to identify known malicious files. These are compared with hash databases, which contain hashes of known malware. This enables investigators to quickly determine if a file is harmful without having to open or execute it.
Key Tools for Hashing in Digital Forensics
1. Kali Linux
Kali Linux, a popular Linux distribution for digital forensics, comes pre-loaded with tools like sha256sum, md5sum, and other command-line utilities that allow quick and efficient hashing. Forensics professionals use these tools to verify the integrity of evidence files and confirm that files haven’t been altered during acquisition and analysis.
Usage:
sha256sum <filename> # Generate SHA-256 hashmd5sum <filename> # Generate MD5 hashAdvantages: Kali Linux provides a straightforward way to hash files with reliable algorithms, making it an essential tool for forensic verification.
2. OpenSSL
OpenSSL is a powerful cryptographic toolkit available on most Linux distributions. It supports various hashing algorithms and is often used for command-line hashing on Kali and other Linux systems.
Usage:
openssl dgst -sha256 <filename> # Generate SHA-256 hash
openssl dgst -md5 <filename> # Generate MD5 hashAdvantages: OpenSSL’s versatility in hash type selection makes it ideal for verifying data integrity across formats.
3. HashMyFiles
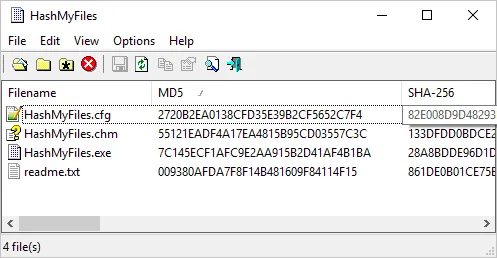
A lightweight Windows-based tool, HashMyFiles supports bulk file hashing, allowing investigators to quickly generate and compare hash values for multiple files.
- Features:
- Calculates MD5, SHA-1, and SHA-256.
- Exports hash data for documentation.
- Advantages: HashMyFiles is user-friendly and provides quick results, ideal for forensic professionals handling bulk data.
Best Practices for Using Hashing in Digital Forensics
Effective hashing follows a few best practices:
- Use Multiple Hashing Algorithms: In addition, forensic experts use multiple hashing algorithms to strengthen their evidence verification. It involves the use of, for example, MD5 and SHA-256, whereby giving another guarantee in case of compromise of a hash.
- Document Hash Values: All evidence needs to be documented in terms of hash values and the record maintained throughout the investigation. Documentation is important to ensure that the chain of custody is maintained and the integrity of the evidence can be shown in court.
- Recalculate Hashes at Key Points: Hash values should be recalculated at critical points-when for example transferring or presenting it in court-proof that data doesn’t change
- Protecting Hash Data and Keys: Hashed data and encryption keys for storage of hashes must be safely kept out of the way from unauthorized access or manipulation. Controlling who can have hash information also lowers the possibility of evidence contamination.
- Regular Updating of Hash Databases: When hashing is applied in the malware detection, forensic teams must refresh their hash databases. Updating these with new hashes of known malware will improve investigators’ malware detection capabilities.
Limitations of Hashing
Hashing is a very fundamental component of digital forensics, yet not without its limitations. First,
- Susceptibility to Collisions: Collisions can be created when two different files result in the same hash, and this is a weakness with some algorithms such as MD5 and SHA-1. The risk with such collisions is lower in stronger algorithms such as SHA-2 and SHA-3.
- Not Encryption: Hashing is not encryption. Hashing proves data integrity but does not encrypt nor protect against unauthorized access to data.
- Susceptibility to Malicious Tampering: Sophisticated attackers will attempt to alter the data in a fashion that results in a known hash, which is a preimage attack. Improvement in the hashing algorithms reduces the danger but not out of the box.
Conclusion
Hashing is one of the vital components of digital forensic analysis. It provides individuals with a reliable and ensured means of maintaining integrity within digital evidence. This helps in preserving the evidence as it is acquired up to the time of presentation with the help of algorithms like MD5, SHA-1, and SHA-2. In addition, best practices in investigators ensure that hash values are recorded for evidence files and updating their databases of malware hashes also reinforces the data integrity. Despite the limitations, hashing remains one of the best methods applied in digital forensics since it is helping experts to attain justice through the preservation of digital evidence integrity.