One of the fundamentals of digital forensics is the chain of custody, holding the evidence whole and airtight from commencement up to investigation finality. Whether it is cyber threats or suspected data breach, it is the handling of the evidence that can break a case. This blog aims to dispense with reasons why the same chain of custody is critical to the admissibility of the same at law and the reliability thereof, along with implications it carries for forensic investigations and their outcome in courts.
What is Chain of Custody?
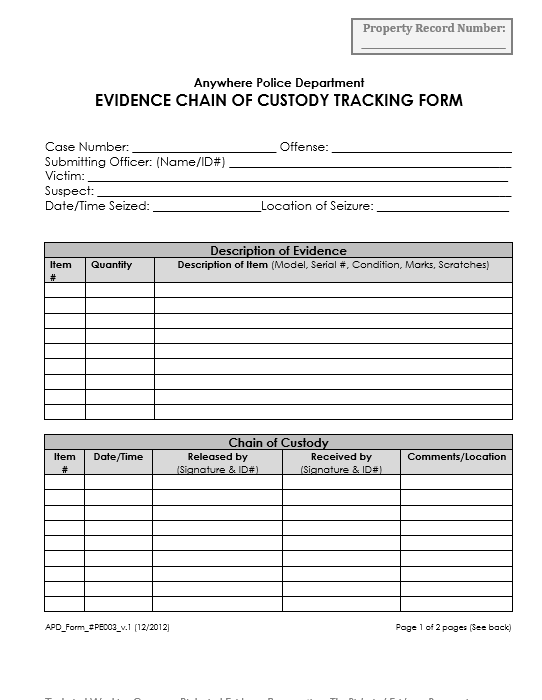
The chain of custody refers to the chronological documentation or paper trail that records the handling, transfer, and analysis of digital evidence from the moment it is collected to its presentation in court. This process involves tracking:
- Who collected the evidence.
- When and where it was collected.
- How it was transferred or stored.
- Who accessed it during the investigation.
- Any changes made to the evidence during its lifecycle.
Maintaining a clear and unbroken chain of custody is crucial to ensure that evidence remains untampered with and its authenticity is preserved.
Why Chain of Custody Matters?
- Legal Admissibility
Evidence must meet legal standards to be accepted in court. A well-maintained chain of custody ensures the evidence hasn’t been tampered with, making it admissible. - Preserving Evidence Integrity
Digital evidence is easily altered. A clear chain of custody shows the evidence remained unchanged throughout the investigation. - Preventing Spoilation
By documenting who accessed the evidence and when, the chain of custody prevents accusations of evidence destruction or alteration. - Accountability and Transparency
It holds everyone handling the evidence accountable and provides transparency in case any issues arise during the investigation. - Defending Against Legal Challenges
A strong chain of custody helps refute challenges to the authenticity of the evidence, proving it was handled properly and remains intact.
Steps to Maintain a Strong Chain of Custody
- Document Every Step
Every action taken with the evidence—whether it’s collection, transfer, analysis, or storage—must be meticulously documented. This includes noting the time, date, location, and individuals involved in each step. - Use Secure Storage Methods
Evidence should be stored in secure environments to prevent unauthorized access or tampering. Digital evidence, such as hard drives or flash drives, must be stored in tamper-evident containers or sealed evidence bags to prevent manipulation. - Limit Access to Evidence
Only authorized personnel should be allowed to handle the evidence. Limiting access reduces the risk of accidental or intentional alterations. Anyone accessing the evidence should be logged in the chain of custody record. - Use Hashing Techniques
One of the most effective methods of ensuring the integrity of digital evidence is to use hashing algorithms, such as MD5 or SHA-256. These algorithms generate unique “digital fingerprints” for a file. If the hash value changes at any point, it indicates that the evidence has been altered. - Follow Proper Transfer Protocols
Whenever evidence is transferred from one person or location to another, the transfer should be recorded, and all parties involved should sign off on the transfer. This ensures there is a clear and accountable record of the evidence’s movement.
Real-World Consequences of Failing the Chain of Custody
Failing to maintain a proper chain of custody can have serious consequences, both in criminal cases and corporate investigations. For example, if digital evidence related to a cybercrime is compromised due to a broken chain of custody, the accused party may be acquitted on a technicality, allowing them to evade justice. In a corporate setting, a flawed chain of custody can jeopardize internal investigations, leading to reputational damage, financial loss, or failed litigation.
Conclusion
In digital forensics, the chain of custody is not just a procedural formality—it is the backbone of evidence integrity and legal admissibility. A strong, well-maintained chain of custody ensures that digital evidence can be trusted, protects the investigation from legal challenges, and upholds the principle of justice. By rigorously adhering to best practices in documenting and handling digital evidence, forensic professionals can safeguard the truth and ensure that justice is served.